It’s been quite a number of busy weeks since my last post … pheeeew … real life can be so demanding. Not only just a personal life, there are also many bussines and intricacy at work that draw a lot of my attention lately. C’est La Vie 🙂 … but from now on … my troubles would be out of sights 🙂 Let your heart be light … have yourself a merry little Christmas 🙂
Ok, this time I would like to share some steps how to root the Axioo Picopad running on Android Froyo. Bassicaly this is taken from this source and the below steps are for linux just in case some of you doesn’t have winblows (like me) and want to root the picopad for running some extra apps that need a root privilege. Please remember, honestly, you do not need to do this if you had no intention to run some application that need root privileges. Do this on your own risk, cause somehow this rooting process also open another hole called vulnerability, google them and you know why 🙂 There are a good reason behind why google doesn’t give this root capabilities by default on all android devices. If only you know what you have gonna do with this rooting … let’s continue.
Using CLI :
Before attempt to begin typing this below command :
- Please make sure you already had an android debugging tools and the SDK. Download the source from here and follow the instruction on the site.
- Enable the USB debugging function on the picopad device by enabling it under Settings > Applications > Development
- Download the SuperOneClick zip file and extract them to some folder, I place them on project/android/rageagainstthecage under my home folder.
Now you ready to begin :
{code}
[root@jfwork1 ~]# cd /home/jfdesign/project/android/rageagainstthecage
[root@jfwork1 rageagainstthecage]# adb push rageagainstthecage /data/local/tmp
92 KB/s (5392 bytes in 0.057s)
[root@jfwork1 rageagainstthecage]# adb push su /data/local/tmp
139 KB/s (22120 bytes in 0.154s)
[root@jfwork1 rageagainstthecage]# adb push Superuser.apk /data/local/tmp
378 KB/s (38823 bytes in 0.100s)
[root@jfwork1 rageagainstthecage]# adb shell
$ cd data/local/tmp
$ ls
Superuser.apk
su
rageagainstthecage
data
fs_type
mount
hotplug
loading
$ ./rageagainstthecage
./rageagainstthecage: permission denied
$ chmod 775 rageagainstthecage
$ ./rageagainstthecage
[*] CVE-2010-EASY Android local root exploit (C) 2010 by 743C
[*] checking NPROC limit …
[+] RLIMIT_NPROC={3240, 3240}
[*] Searching for adb …
[+] Found adb as PID 86
[*] Spawning children. Dont type anything and wait for reset!
[*]
[*] If you like what we are doing you can send us PayPal money to
[*] [email protected] so we can compensate time, effort and HW costs.
[*] If you are a company and feel like you profit from our work,
[*] we also accept donations > 1000 USD!
[*]
[*] adb connection will be reset. restart adb server on desktop and re-login.
$ [root@jfwork1 rageagainstthecage]#
{/code}
the picopad device will reboot and the adb server connection will disconnect. Connect again after the device ready.
{code}
[root@jfwork1 ~]# adb shell
# cd /data/local/tmp
# mount
rootfs / rootfs rw,relatime 0 0
tmpfs /dev tmpfs rw,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
/dev/block/mtdblock7 /system yaffs2 rw,relatime 0 0
/dev/block/mtdblock10 /data yaffs2 rw,nosuid,nodev,relatime 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
/dev/block/mtdblock1 /misc yaffs2 rw,nosuid,nodev,relatime 0 0
/dev/block/mtdblock5 /hidden yaffs2 rw,nosuid,nodev,relatime 0 0
/dev/block/mtdblock9 /cache yaffs2 rw,nosuid,nodev,relatime 0 0
/dev/block/mtdblock8 /misc2 yaffs2 rw,nosuid,nodev,relatime 0 0
debugfs /sys/kernel/debug debugfs rw,relatime 0 0
/dev/block/vold/179:1 /mnt/sdcard vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0702,dmask=0702,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:1 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0702,dmask=0702,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
tmpfs /mnt/sdcard/.android_secure tmpfs ro,relatime,size=0k,mode=000 0 0
/dev/block/dm-0 /mnt/asec/com.android.BlackMarketApp-1 vfat ro,dirsync,nosuid,nodev,noexec,relatime,uid=1000,fmask=0222,dmask=0222,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/dm-1 /mnt/asec/org.xbmc.android.remote-1 vfat ro,dirsync,nosuid,nodev,noexec,relatime,uid=1000,fmask=0222,dmask=0222,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/dm-2 /mnt/asec/com.com2us.sliceit-2 vfat ro,dirsync,nosuid,nodev,noexec,relatime,uid=1000,fmask=0222,dmask=0222,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/dm-3 /mnt/asec/com.rovio.angrybirds-1 vfat ro,dirsync,nosuid,nodev,noexec,relatime,uid=1000,fmask=0222,dmask=0222,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/dm-4 /mnt/asec/com.rechild.advancedtaskkillerpro-1 vfat ro,dirsync,nosuid,nodev,noexec,relatime,uid=1000,fmask=0222,dmask=0222,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
# mount -o remount,rw -t yaffs2 /dev/block/mtdblock7 /system
# cat su > /system/bin/su
# cat Superuser.apk > /system/app/Superuser.apk
# chmod 06777 /system/bin/su
# chmod 777 /system/app/Superuser.apk
# reboot
[root@jfwork1 ~]#
{/code}
After reboot … done ! You have rooted.
Using Mono
The 2nd method is using mono for linux to run SuperOneClick.exe winblows program to run on linux os. Just like the above steps, please make sure you already had the adb tools installed on the system and also enabling the USB debugging function on the picopad device. This steps also needs the mono application and the Implementation of Microsoft’s UI Automation which later dealing with windows form under mono environment. Don’t worry, if you’re using KLIXs I already package them so you can download from synaptic, install them and you can directly using it. Open the synaptics package manager, reload the package list and install these apps :
- libncurses5 and libstdc++5
- mono and mono-winforms
Once they were Mark for Installation they also retrive other library needed, just choose agree and click Apply.
Now, open the konsole, change to the extracted SuperOneClick program and execute that using mono :
{code}[jfdesign@jfwork1 ~]$ cd project/android/superoneclick/
[jfdesign@jfwork1 superoneclick]$ mono SuperOneClick.exe{/code}
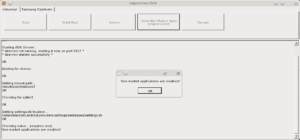
Just press the Root Button and wait until finish, and done !! you have rooted. You can also enable to Allow Non market Apps installation for your picopad so you get another freedom of choosing the non market apps around the net.
Another options :
For you that have a winblows you can use directly the winblows exe version of SuperOneClick application from the original link mention above, extract them to some location, plug in the picopad usb and run the Superoneclick.exe. The SuperOneClick tools was made by CLShortFuse from xda-dev, great work! The process was self explanatory since there is only click a single button 🙂 … and you have Rooted ! Easy and nothing can be learn or explain.
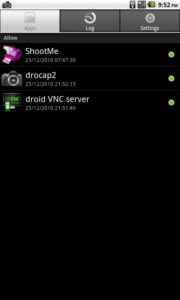
Here is the screenshot using drocap2 the Superuser.apk after rooted :
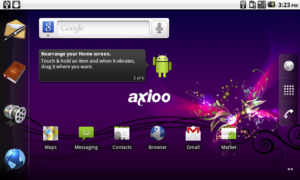
 And here is the screenshot the main screen of Axioo PicoPad :
And here is the screenshot the main screen of Axioo PicoPad :
 And here is side by side with bravlon powered by Sandy Bridge :
And here is side by side with bravlon powered by Sandy Bridge :